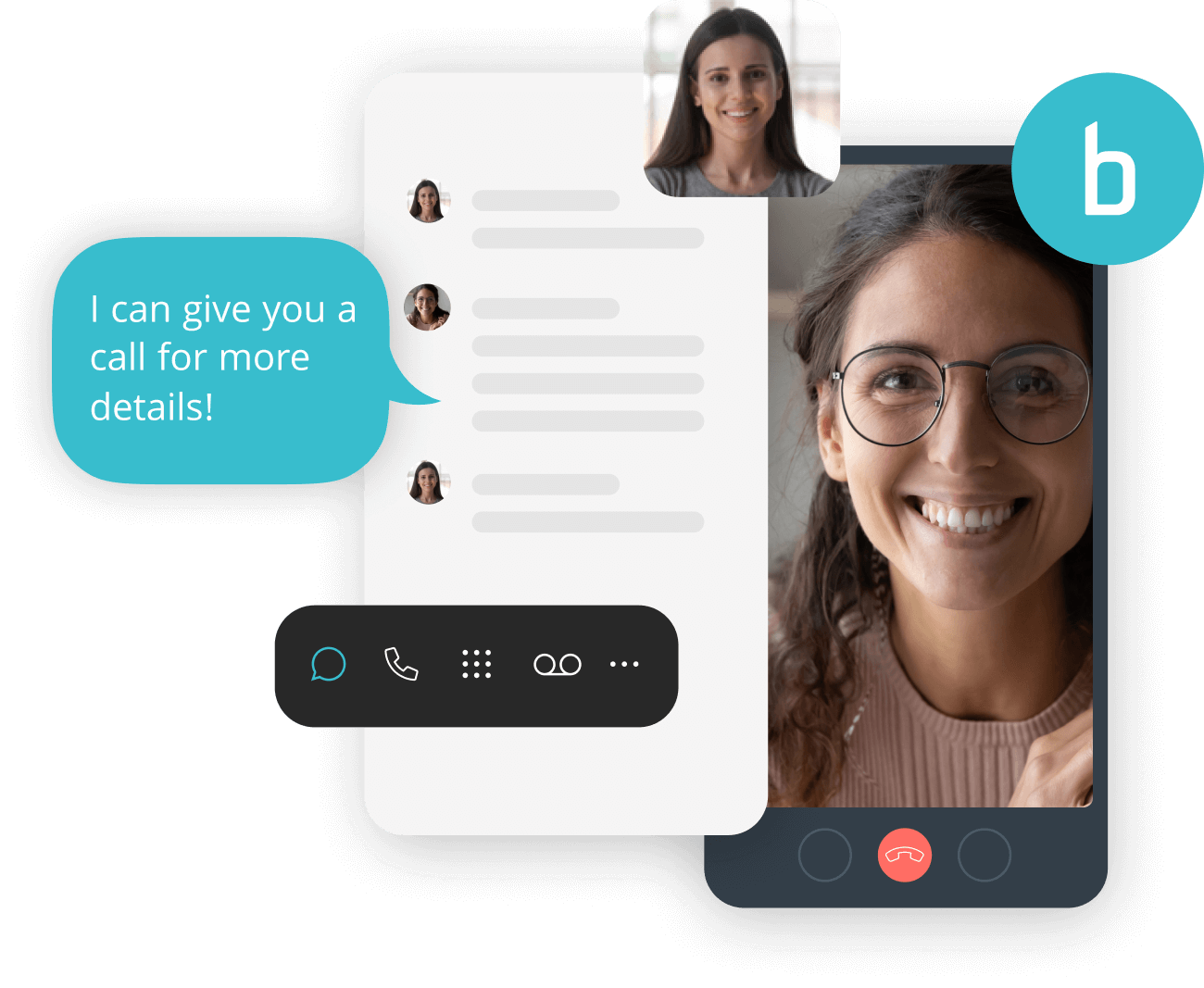
The all-in-one platform for great conversations.
With a single phone service app for calling, video, text, collaboration, voicemail and fax, you can always come through for your customers and teammates.

Connected teams build stronger businesses.
Communicator is where conversations happen quicker, customer issues resolve in record time and your team can collaborate like never before.
A Single Interface
Call, text, chat, and video conference with customers and teammates from the same phone service app.
Redesigned & Improved
Included with b-hive
Made to help your team succeed.

Provide better customer experiences.
- Call, text, and video conference with customers and clients using your business phone number.
- Switch from one mode of communication to the other seamlessly.
- Use traditional phone features like mute, hold and blind call transfer.
- Share your screen and files.
New ways for your team to collaborate.
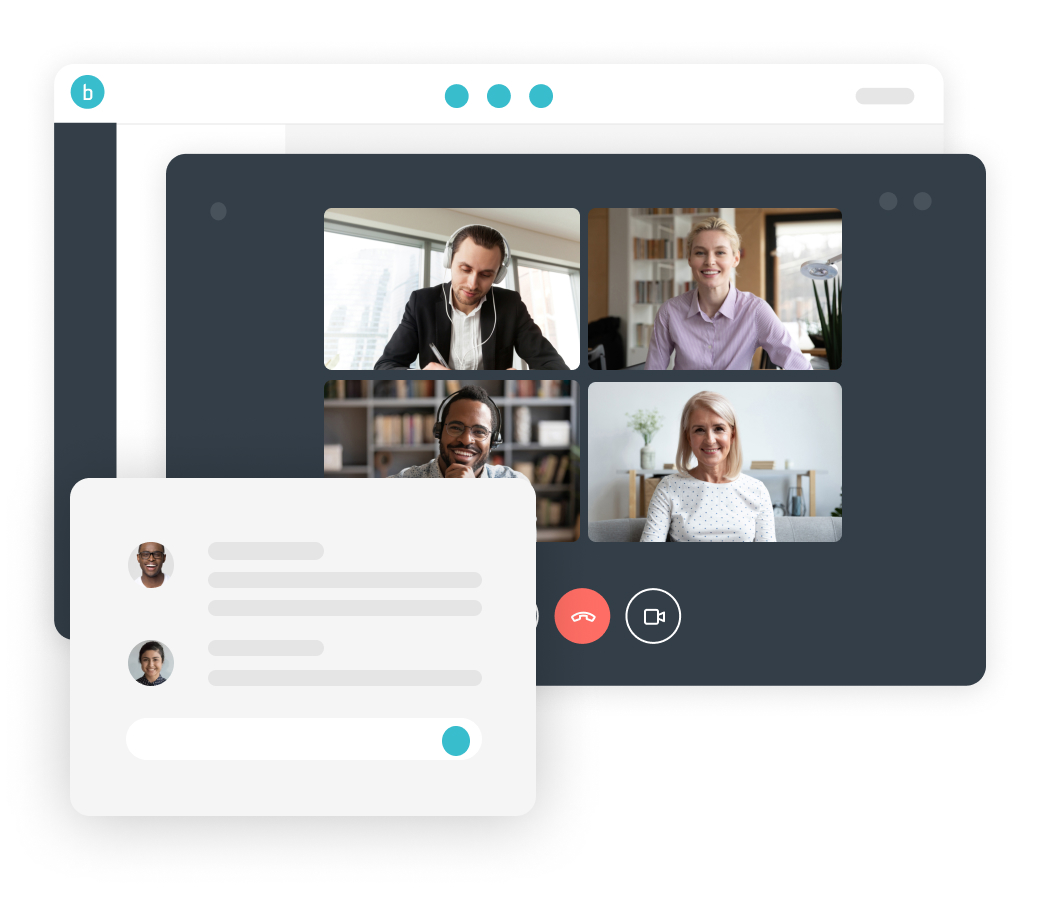
- Collaborate, chat, video conference and call one-on-one or in groups.
- Updated video conferencing supports up to 50 simultaneous users.
- Personal links for individual video rooms and unique links for scheduling future meetings.
- Calendar plugin for easily adding meeting links to your calendar invitations.
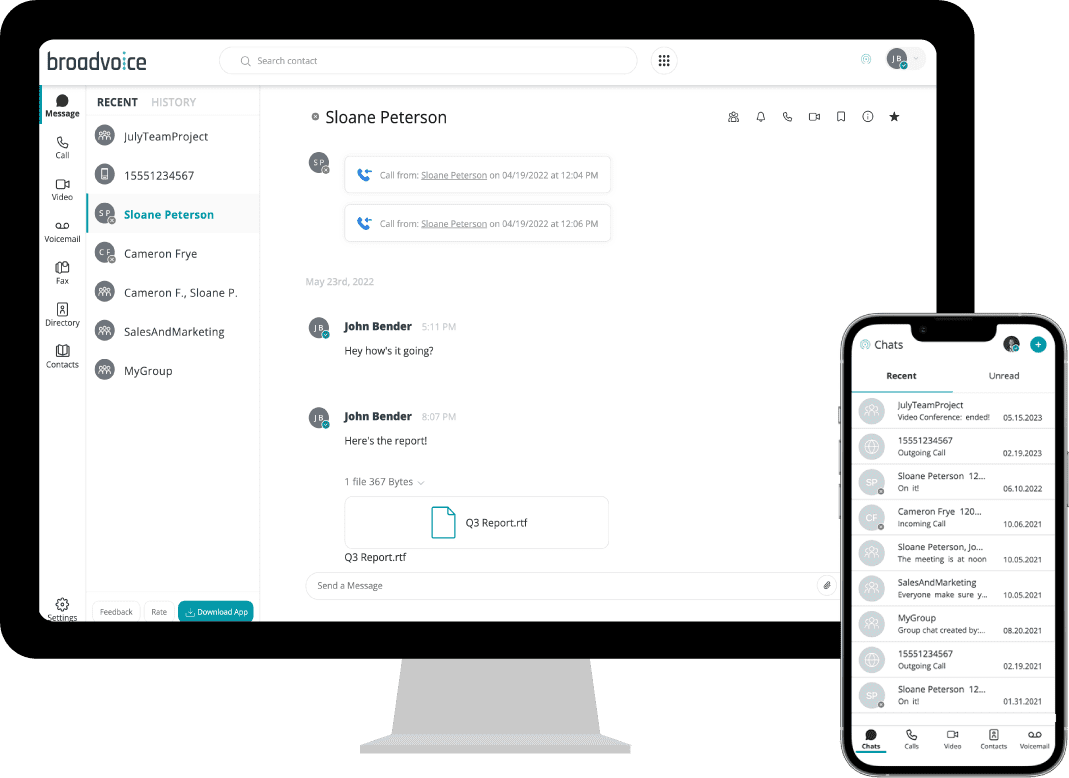
- Access your full company directory with numbers, extensions, and email addresses.
Included with b-hive.
Communicator is the softphone interface for b-hive, so it works with your business number, and all call data and settings sync with the b-hive web portal.
Everything you need to communicate and collaborate.
See why our customers love b-hive.
Ready to modernize your communications?
We’ll walk you through how b-hive and Communicator can help you grow your business with a personal demonstration.
Want to explore Communicator in more detail?
Communicator Overview
View the flyer for b-hive Communicator